Not even to my desk
Updated: 2010-08-31 16:26:20
Walking into work through the South Lobby this morning I passed three monitors that normally have traffic, weather and footage from a traffic camera. The traffic monitor displays traffic information from WTOP normally, but today it showed cgidoctor.com. This page advised the user on how to remove fake antivirus infections. Links to remove fake antivirus [...]

 Gmail users who run Google Chrome are up in arms today following the launch of the new Gmail priority inbox service.
Not because the feature doesn't work for internet users who've chosen the Chrome browser to access their email, but because Google appears to have promoted the service in a cack-handed way which has scared some [...]
Gmail users who run Google Chrome are up in arms today following the launch of the new Gmail priority inbox service.
Not because the feature doesn't work for internet users who've chosen the Chrome browser to access their email, but because Google appears to have promoted the service in a cack-handed way which has scared some [...]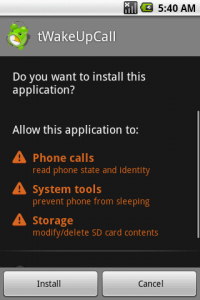 So you've been hearing lately about how some Android applications are going rogue, and being used to steal user's data and infiltrate their phones, to sit idly by only to wreak havoc when the user least expects it (ok, so maybe I exaggerated a little there). But there has been a lot of buzz lately about certain apps not playing by the rules, or including certain calls to leach user information. A lot of this buzz has been spun as backlash against Google for allowing these types of applications to exist (instead of having some asininely draconian filtering process like some 'other' phone provider).
So you've been hearing lately about how some Android applications are going rogue, and being used to steal user's data and infiltrate their phones, to sit idly by only to wreak havoc when the user least expects it (ok, so maybe I exaggerated a little there). But there has been a lot of buzz lately about certain apps not playing by the rules, or including certain calls to leach user information. A lot of this buzz has been spun as backlash against Google for allowing these types of applications to exist (instead of having some asininely draconian filtering process like some 'other' phone provider).